This weekend has seen a massive cyberattack against large corporations and public institutions. Negligence on the part of governments and companies allowed hackers to encrypt data on hundreds of thousands of computers based on tools developed by US security NSA.
In March, Wikileaks released 8,761 documents relating to the hacking activities of the CIA, highlighting the risk that the cyber warfare departments of the intelligence agencies posed to internet security. The leak consisted of a set of hacking tools called “Vault 7” that was mainly used to spy on allies and industrial espionage. This included tools to hack into internet connected computers, Mac computer, windows computers, internet connected devices (baby monitors, CCTV cameras, routers, printers etc), as well as private networks without internet connection (government departments, multinational corporations etc).
The tools enabled CIA agents and contractors (employed by private companies) to access a shared repository of hacking tools that could be used to infect target computers and networks.
I feel like this sums up my whole weekend. pic.twitter.com/gPOKYiEW9e
— Kevin Beaumont (@GossiTheDog) May 14, 2017
Most controversially, it included so called 0-day exploits, which are unpatched security flaws in commonly used software. This was a breach of a promise made by the US intelligence community to notify software and hardware manufacturers of any flaw that they found, so that a patch could be released. By keeping these exploits to themselves, and placing them all together in a poorly guarded treasure trove for hackers they imperilled millions if not billions of devices around the world.
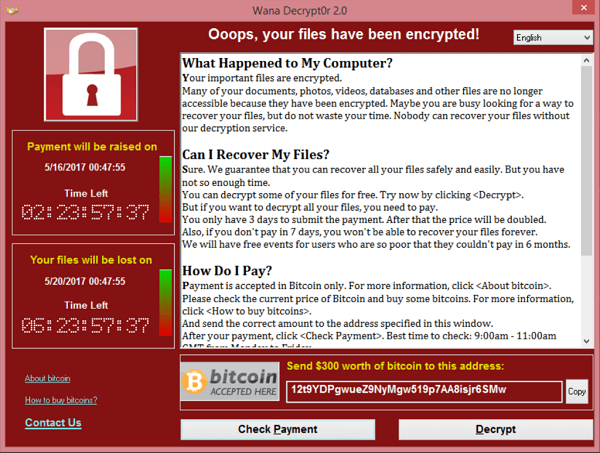
The size of the threat was revealed over the weekend, when almost 200,000 computers were affected by the WannaCry ransomware. A ransomware is basically a piece of software that encrypts all the files on the infected computer and asks the owner to pay money to the hacker in order to get the files back. In addition, there’s a worm that helps spread the ransomware from the infected computer to others, typically using emails or social media, and in this case, vulnerabilities in the computer network that it has infiltrated.
This particular worm was based not on Vault 7 of the CIA, but on files that came out of the NSA (possibly the notorious Equation Group), and somehow found itself into the hands of the hacking group Shadowbrokers, who published at least some of the exploits in April.
The particular vulnerability that was used by the WannaCry related to Windows file sharing mechanism. A patch for it was released in March. Presumably, the NSA after realising that the exploit had been leaked, decided it was time to tell Microsoft about it. The question is, for how many months or years were they sitting on this information, the knowledge of a critical security flaw in one of the most used operating systems in the world without telling anyone about it? Not only that, they obviously didn’t keep their tools very secure.
No computer code or computer system can ever be 100% safe. A hacker can always imagine different ways of subverting perfectly harmless code to accomplish a nefarious task. Good coding practices helps (Windows is notoriously bad at that) but the software developer is always faced with millions of people who try to subvert the code, and coming up with imaginative ways of accomplishing that. For that reason, software companies rely on reports from anti-virus companies, security companies, infected computers and volunteers to report on vulnerabilities. Anytime someone finds an exploit in the software and doesn’t report it, it magnifies the risk when they share it with others. If they on top of that develop software to use those exploits, then they are effectively spreading new techniques in the wild, enabling other hackers to figure out what they have done. This is the case even if their treasure trove of exploits isn’t released in the wild like has happened with the NSA repository and the CIA’s vault 7.
What is entirely clear is that it’s complete nonsense to say that the activities of the intelligence agencies, and their mass surveillance methods, is only a problem if you are guilty of a crime. The backdoors (to circumvent encryption for example) they ask of software developers and the exploits they store and develop add to the risks faced by internet users. Rather than helping making the internet a more secure place, they are making it more unsafe.
Furthermore, from the Wikileaks documents on Vault 7, the targets of these attacks are not “terrorists”, as is often claimed to justify these types of activities. Rather, it’s foreign governments and companies, including supposed allies. Wikileaks hasn’t released the list, but here’s how they describe it:
“Among the list of possible targets of the collection are 'Asset', 'Liason Asset', 'System Administrator', 'Foreign Information Operations', 'Foreign Intelligence Agencies' and 'Foreign Government Entities'. Notably absent is any reference to extremists or transnational criminals.”
So, the purpose of these activities is not law enforcement or protection at all, but to give US companies and US diplomats the upper hand in competition with other states.
Russian railway ops centre Wanna Cry. pic.twitter.com/Xc3eibMOf1
— Kevin Beaumont (@GossiTheDog) May 14, 2017
This means that patients in health care in the UK, Telefonica customers in Spain and Russian train passengers have had their lives put at risk or disrupted on a massive scale because the US government wants Boeing to get the upper hand in competition with Airbus in getting orders.
As the economic crisis intensifies, and protectionism comes even more on the order of the day, we’re likely to see even more of this type of attacks.
In October, it remains unclear for what purpose, internet infrastructure was attacked by millions of small internet connected devices. This attack might have been by some amateur group of hackers, but perhaps more likely an organised attempt by a large institution. It is an open secret that not only US, but also Russian, Israeli and Chinese intelligence agencies have hacked into and infected hundreds of thousands of computers in order to give their companies or diplomats an advantage.
Companies and governments in the rush to save money also fail to make the simplest of security measures. The manufacturers of small internet connected devices often use default passwords for their devices such as “administrator” and “password”, meaning that hackers can get into these devices with particular ease. This does not just compromise the privacy of the user of the device (finding their private images all over the internet for example) but also poses a threat to everyone if a hacker should take it over and use it in attacks.
The irresponsible way in which governments and companies act puts in jeopardy the entire existence of the Internet. It threatens to parcel it up within national borders (as has already happened to a large extent with China). This will eradicate one of the most significant technological achievements over the past 20 years.
The only way to combat this is to disarm the security services, publish all their exploits (after giving some time for software manufacturers to patch their software), publish the source code of Windows and other software publicly for inspection. The biggest software companies should be nationalised and put under workers’ control. No more discovered and unpatched security flaws. Co-operation between countries and companies is the only way forward. Taking the profit motive out of the Internet is the only way to secure its long term future.